The Role of IEC 62443 in Modern Cybersecurity – In today’s digital era, cybersecurity has become a top priority for industries worldwide. With more organizations relying on connected systems, the risk of cyber threats has significantly increased.
Standards like IEC-62443 offer essential frameworks to protect critical infrastructure and sensitive data. These guidelines help companies build secure systems that defend against potential breaches, providing a structured approach to manage cybersecurity risks effectively.
Cybersecurity standards are crucial for creating a safe digital environment. IEC-62443 focuses on both technical safeguards and organizational practices, ensuring comprehensive protection.
By implementing these standards, industries can secure their systems, protect valuable data, and improve overall resilience against evolving cyber threats. As digital transformation continues, adopting these standards is key for maintaining safe, efficient operations.
The Backbone of Cybersecurity Standards
Protecting assets from cyber dangers is crucial during the age of digital growth. One of the standards, IEC-62443, is essential in establishing robust cybersecurity frameworks. These standards are relevant across various industries, especially in sectors reliant on complex systems.
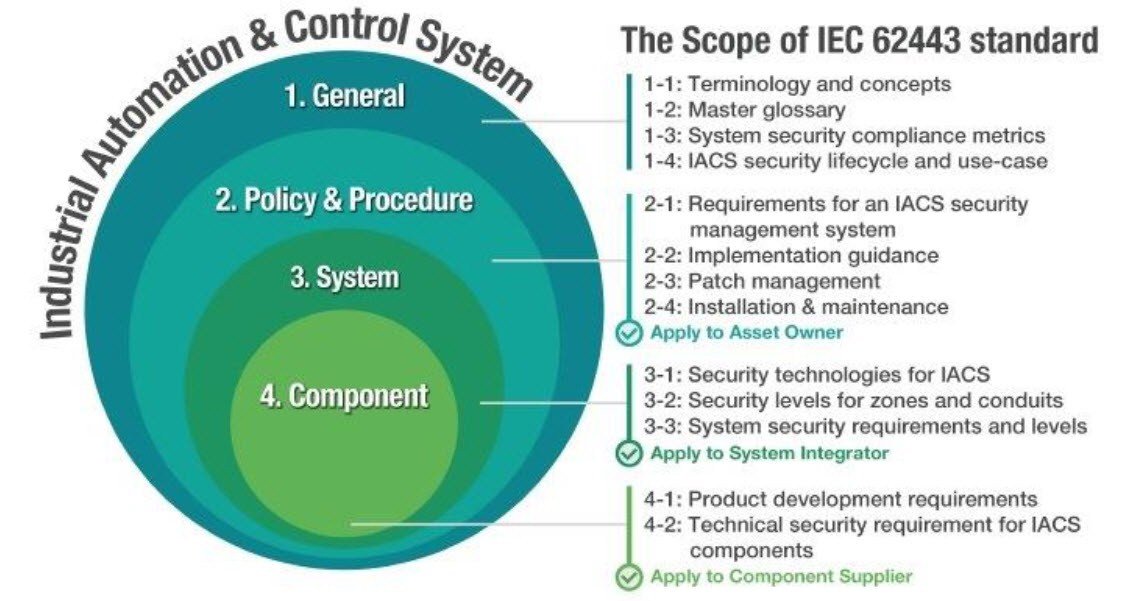
They provide actionable guidelines that help industries create and maintain secure environments, protecting critical infrastructure and sensitive data from potential breaches. By implementing these standards, organizations gain the ability to systematically assess and mitigate risks, ensuring a heightened level of security.
The significance of such standards lies in their comprehensive approach. They encompass not only technical measures but also organizational procedures.
This dual focus ensures that all security aspects are addressed, from physical barriers to employee awareness programs. As the cybersecurity landscape evolves, having detailed frameworks is essential to navigate and preempt threats effectively, a necessity recognized by industrial leaders worldwide.
Adapting to New Threats in Industrial Control Systems
Modern industries increasingly rely on interconnected control systems, which, unfortunately, are attractive targets for cybercriminals. Industrial systems need comprehensive protection strategies, with complex machinery and intricate processes at their core.
Companies can take the necessary steps to safeguard these systems from disruption. The consequences of a breach can have a devastating impact on safety and productivity.
These threats are ever-evolving, but proactive measures, such as timely updates and continuous monitoring, help mitigate them. Integrating IEC 62443 standards into organizational policies ensures protection is built into every control system layer.
It includes securing communication networks, safeguarding remote access, and implementing stringent identity verification protocols. Each of these steps works collectively to fortify industrial operations against cyber threats.
Implementing Effective Cybersecurity Measures
Effective cybersecurity implementation is not a one-time task but a continuous endeavor. Organizations must adopt an ongoing improvement process, integrating new technologies, refining policies, and combating novel threats.
It starts with developing a comprehensive security framework tailored to the organization’s needs based on well-established standards. Compliance with global standards is not merely a regulatory requirement but a business imperative.
Organizations can guarantee data integrity and system reliability by being proactive instead of reactive. Regular system audits, penetration testing, and employee training initiatives create a robust defense mechanism against potential cyber threats. These methods allow companies to tackle weaknesses proactively instead of simply reacting to problems as they arise.
When Standards Meet Technology
The marriage of cutting-edge technology and cybersecurity standards is critical in today’s digital environment. Technologies such as AI, machine learning, and blockchain are revolutionizing security approaches, offering unprecedented opportunities to safeguard digital infrastructures. By integrating these technologies with IEC 62443 standards, industries can establish enhanced security protocols and react swiftly to perceived threats.
By leveraging these insights, organizations can adopt a proactive stance, addressing threats before they materialize into significant issues. Similarly, blockchain technology provides immutable records that enhance data integrity, making it difficult for unauthorized parties to alter sensitive information. Industries gain a fortified stance against cyber threats by strategically combining these technologies with established standards.
Challenges in Maintaining Cybersecurity Protocols
- Keeping up with evolving threats.
- Ensuring consistent compliance across the board.
- Maintaining system integrity during updates.
Navigating the dynamic landscape of cybersecurity involves overcoming several challenges. Cyber threats evolve at a rapid pace, often outstripping conventional security measures. Continuous vigilance and adaptation are essential to anticipate and counteract new attack methods. The need for consistent compliance across various departments can further complicate matters, as inconsistencies often create vulnerabilities.
Additionally, maintaining system integrity during updates presents another significant challenge. Mismanaged updates can result in system downtime or introduce new security gaps. Organizations must develop and sustain careful update protocols to ensure system improvements do not inadvertently compromise security. It requires a meticulous balance between maintaining operational continuity and achieving high-level protection standards.
Building a Culture of Cybersecurity
Establishing a cybersecurity culture in a company is essential for improving defense mechanisms against cyber threats. This culture emphasizes mindfulness and vigilance among all employees, ensuring everyone understands their role in maintaining security. Regular training sessions, awareness campaigns, and the reinforcement of best practices are all integral to fostering such a culture.
Organizations should also encourage open communication regarding potential cybersecurity threats and incidents. This openness enables quick responses and collaborative problem-solving, which are critical components in maintaining robust defenses. By cultivating a proactive cybersecurity culture, businesses can reduce their vulnerability to cyber threats and establish a united front in the fight against cybercrime.
Real-Life Lessons from Major Cybersecurity Breaches
Analyzing past cybersecurity breaches provides crucial insights into the importance of robust security frameworks. These events show us what can go wrong when comprehensive systems are not in place. Resources highlight numerous cases where inadequate security measures led to significant financial and reputational damage.
By studying these incidents, industries can learn valuable lessons about the importance of real-time monitoring, immediate response plans, and integrating global standards. Understanding these lessons not only aids in preventing similar occurrences in the future but also sharpens an organization’s overall cybersecurity strategy, making it more resilient and prepared for unexpected challenges.
Future Outlook on Industrial Cybersecurity Standards
The future of industrial cybersecurity lies in the collaborative efforts of organizations, regulators, and technology innovators. As industries continue to digitalize, the reliance on solid cybersecurity frameworks will expand. Predictive analytics and AI will become standard tools in the cybersecurity arsenal, helping businesses predict and preemptively respond to emerging threats.
Standards like IEC 62443 will evolve in parallel with technological advancements, ensuring that industries remain protected against novel threats. By staying informed about potential vulnerabilities and actively adopting new security technologies, organizations can secure their operations today and anticipate and adapt to the challenges of tomorrow’s digital landscape.